




The practice of using a name as a humanly more meaningful abstraction of a host's numerical address on the network dates back to the ARPANET era. Before the DNS was invented in 1983, each computer on the network retrieved a file called HOSTS.TXT from a computer at SRI (now SRI International). The HOSTS.TXT file mapped names to numerical addresses. A hosts file still exists on most modern operating systems, either by default or through explicit configuration. Many operating systems use name resolution logic that allows the administrator to configure selection priorities for available DNS resolution methods.
The rapid growth of the network required a scalable system that recorded a change in a host's address in one place only. Other hosts would learn about the change dynamically through a notification system, thus completing a globally accessible network of all hosts' names and their associated IP addresses.
At the request of Jon Postel, Paul Mockapetris invented the Domain Name System in 1983 and wrote the first implementation. The original specifications appeared in RFC 882 and RFC 883 which were superseded in November 1987 by RFC 1034 and RFC 1035. Several additional Request for Comments have proposed various extensions to the core DNS protocols.
In 1984, four Berkeley students—Douglas Terry, Mark Painter, David Riggle and Songnian Zhou—wrote the first UNIX implementation, which was maintained by Ralph Campbell thereafter. In 1985, Kevin Dunlap of DEC significantly re-wrote the DNS implementation and renamed it BIND—Berkeley Internet Name Domain. Mike Karels, Phil Almquist and Paul Vixie have maintained BIND since then. BIND was ported to the Windows NT platform in the early 1990s.
BIND was widely distributed, especially on Unix systems, and is the dominant DNS software in use on the Internet. With the heavy use and resulting scrutiny of its open-source code, as well as increasingly more sophisticated attack methods, many security flaws were discovered in BIND. This contributed to the development of a number of alternative nameserver and resolver programs. BIND itself was re-written from scratch in version 9, which has a security record comparable to other modern Internet software.
The DNS protocol was developed and defined in the early 1980s and published by the Internet Engineering Task Force.
How Domain Name Servers Work????
You spend any time on the Internet sending e-mail or browsing the Web, then you use domain name servers without even realizing it. Domain name servers, or DNS, are an incredibly important but completely hidden part of the Internet, and they are fascinating. The DNS system forms one of the largest and most active distributed databases on the planet. Without DNS, the Internet would shut down very quickly.
When you use the Web or send an e-mail message, you use a domain name to do it. For example, the URL "http://www.howstuffworks.com" contains the domain name howstuffworks.com. So does the e-mail address "iknow@howstuffworks.com."
Human-readable names like "howstuffworks.com" are easy for people to remember, but they don't do machines any good. All of the machines use names called IP addresses to refer to one another.
For example, the machine that humans refer to as "www.howstuffworks.com" has the IP address 70.42.251.42. Every time you use a domain name, you use the Internet's domain name servers (DNS) to translate the human-readable domain name into the machine-readable IP address. During a day of browsing and e-mailing, you might access the domain name servers hundreds of times!
In this article, we'll take a look at the DNS system so you can understand how it works and appreciate its amazing capabilities.
STRUCTURE OF DNS
The domain name space
The hierarchical domain name system, organized into zones, each served by a name server.
The domain name space consists of a tree of domain names. Each node or leaf in the tree has zero or more resource records, which hold information associated with the domain name. The tree sub-divides into zones beginning at the root zone. A DNS zone consists of a collection of connected nodes authoritatively served by an authoritative nameserver. (Note that a single nameserver can host several zones.)
Administrative responsibility over any zone may be divided, thereby creating additional zones. Authority is said to be delegated for a portion of the old space, usually in form of sub-domains, to another nameserver and administrative entity. The old zone ceases to be authoritative for the new zone.
Domain name formulation
The definitive descriptions of the rules for forming domain names appear in RFC 1035, RFC 1123, and RFC 2181. A domain name consists of one or more parts, technically called labels, that are conventionally concatenated, and delimited by dots, such as example.com.
1. The right-most label conveys the top-level domain; for example, the domain name www.example.com belongs to the top-level domain com.
2. The hierarchy of domains descends from right to left; each label to the left specifies a subdivision, or subdomain of the domain to the right. For example: the label example specifies a subdomain of the com domain, and www is a subdomain of example.com. This tree of subdivisions may consist of 127 levels.
3. Each label may contain up to 63 characters. The full domain name may not exceed a total length of 253 characters. In practice, some domain registries may have shorter limits.
4. DNS names may technically consist of any character representable in an octet (RFC 3696). However, the allowed formulation of domain names in the DNS root zone, and most other subdomains, uses a preferred format and character set. The characters allowed in a label are a subset of the ASCII character set, and includes the characters a through z, A through Z, digits 0 through 9, and the hyphen. This rule is known as the LDH rule (letters, digits, hyphen). Domain names are interpreted in case-independent manner. Labels may not start or end with a hyphen, nor may two hyphens occur in sequence.
5. A hostname is a domain name that has at least one IP address associated. For example, the domain names www.example.com and example.com are also hostnames, whereas the com domain is not.
Internationalized domain names
The permitted character set of the DNS prevented the representation of names and words of many languages in their native alphabets or scripts. ICANN has approved the Punycode-based Internationalized domain name (IDNA) system, which maps Unicode strings into the valid DNS character set. In 2009 ICANN approved the installation of IDN county code top-level domains. In addition, many registries of the existing TLDs have adopted IDNA.
Name servers
The Domain Name System is maintained by a distributed database system, which uses the client-server model. The nodes of this database are the name servers. Each domain has at least one authoritative DNS server that publishes information about that domain and the name servers of any domains subordinate to it. The top of the hierarchy is served by the root nameservers, the servers to query when looking up (resolving) a top-level domain name (TLD).
Authoritative name server
An authoritative name server is a name server that gives answers that have been configured by an original source, for example, the domain administrator or by dynamic DNS methods, in contrast to answers that were obtained via a regular DNS query to another name server. An authoritative-only name server only returns answers to queries about domain names that have been specifically configured by the administrator.
An authoritative name server can either be a master server or a slave server. A master server is a server that stores the original (master) copies of all zone records. A slave server uses an automatic updating mechanism of the DNS protocol in communication with its master to maintain an identical copy of the master records.
Every DNS zone must be assigned a set of authoritative name servers that are installed in NS records in the parent zone.
When domain names are registered with a domain name registrar their installation at the domain registry of a top level domain requires the assignment of a primary name server and at least one secondary name server. The requirement of multiple name servers aims to make the domain still functional even if one name server becomes inaccessible or inoperable. The designation of a primary name server is solely determined by the priority given to the domain name registrar. For this purpose generally only the fully qualified domain name of the name server is required, unless the servers are contained in the registered domain, in which case the corresponding IP address is needed as well.
Primary name servers are often master name servers, while secondary name server may be implemented as slave servers.
An authoritative server indicates its status of supplying definitive answers, deemed authoritative, by setting a software flag (a protocol structure bit), called the Authoritative Answer (AA) bit in its responses.This flag is usually reproduced prominently in the output of DNS administration query tools (such as dig) to indicate that the responding name server is an authority for the domain name in question.
Recursive and caching name server
In principle, authoritative name servers are sufficient for the operation of the Internet. However, with only authoritative name servers operating, every DNS query must start with recursive queries at the root zone of the Domain Name System and each user system must implement resolver software capable of recursive operation.
To improve efficiency, reduce DNS traffic across the Internet, and increase performance in end-user applications, the Domain Name System supports DNS cache servers which store DNS query results for a period of time determined in the configuration (time-to-live) of the domain name record in question. Typically, such caching DNS servers, also called DNS caches, also implement the recursive algorithm necessary to resolve a given name starting with the DNS root through to the authoritative name servers of the queried domain. With this function implemented in the name server, user applications gain efficiency in design and operation.
The combination of DNS caching and recursive functions in a name server is not mandatory, the functions can be implemented independently in servers for special purposes.
Internet service providers typically provide recursive and caching name servers for their customers. In addition, many home networking routers implement DNS caches and recursors to improve efficiency in the local network.


Sockets
An AppleTalk socket is a unique, addressable location in an AppleTalk node. It is the logical point at which upper-layer AppleTalk software processes and the network-layer Datagram-Delivery Protocol (DDP) interact. These upper-layer processes are known as socket clients. Socket clients own one or more sockets, which they use to send and receive datagrams. Sockets can be assigned statically or dynamically. Statically assigned sockets are reserved for use by certain protocols or other processes. Dynamically assigned sockets are assigned by DDP to socket clients upon request. An AppleTalk node can contain up to 254 different socket numbers. Figure illustrates the relationship between the sockets in an AppleTalk node and DDP at the network layer.
Figure : Socket clients use sockets to send and receive datagrams.


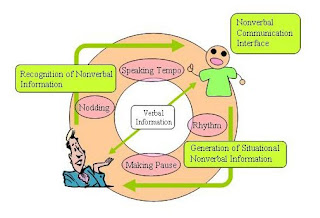 FIG: NON-VERBAL COMMUNICATION
FIG: NON-VERBAL COMMUNICATION
*Visual communication
Visual communication as the name suggests is communication through visual aid. It is the conveyance of ideas and information in forms that can be read or looked upon. Primarily associated with two dimensional images, it includes: signs, typography, drawing, graphic design,illustration, colour and electronic resources. It solely relies on vision. It is form of communication with visual effect. It explores the idea that a visual message with text has a greater power to inform, educate or persuade a person. It is communication by presenting information through visual form. FIG: VISUAL COMMUNICATION
FIG: VISUAL COMMUNICATION